Total Security
Ecosystem
Redefining security beyond boundaries.
A modern security company built to protect what truly matters — people, assets, and data. We bridge the gap between digital and operational protection, creating a unified ecosystem where organizations operate with clarity, safety, and peace of mind.
About Sector
Total Security Ecosystem
Sector is a modern Security Company built to protect what truly matters — people, assets, and data.
We bridge the gap between digital and operational protection, creating a unified ecosystem where organizations can operate with clarity, safety, and peace of mind.
That means combining the precision of cybersecurity, the reliability of on-ground protection, and the discipline of process — all integrated into one seamless system.
One World. One Ecosystem. Total Security
The world no longer separates between digital and physical threats. A cyber breach can open a physical door; a stolen access card can trigger a data leak. Sector exists to unify both worlds.
Digital Security
Protecting networks, data, and infrastructure from unseen threats.
Security Operations
Safeguarding people, facilities, and assets in the physical world.
Integration Layer
Where both converge, forming a unified defense system with shared visibility, intelligence, and response.
Core Principles
Our foundation is built on three core principles that guide every decision we make and every solution we deliver.
Legacy
Long-term security thinking
We understand that your business is more than just operations—it's your legacy. Our long-term security thinking preserves your reputation and ensures business continuity.
- Preserving your reputation
- Ensuring business continuity
- Protecting what you've built
- Generational thinking approach
Helping Self-Control
Empowerment, not fear
Our approach focuses on empowerment, not fear. We're your partner in growth, providing security solutions that enable your business to reach new heights safely.
- Partner in growth
- Security that enables success
- Confidence-building approach
- Complete transparency
Empathy Over Ego
Calm precision under chaos
Process over panic. Calm precision under chaos. Strength through discipline. Transparent security processes that put you in control.
- Process over panic
- Calm precision under pressure
- Disciplined approach
- Transparent processes
PEACE OF MIND
Sleep soundly knowing your digital assets are protected by a team that truly cares about your business success and long-term security.
Protecting the Invisible
Comprehensive digital security services to protect your networks, data, and infrastructure from cyber threats.
Cyber Protect ServicesIdentify vulnerabilities before attackers do
- Web, Mobile, and API Penetration Testing
- Network (Internal & External) Penetration Testing
- Cloud Penetration Testing
- Red Team Simulation of Real-World Attacks
Cyber Detect ServicesContinuous protection through real-time monitoring
- Managed Security Information & Event Management (SIEM)
- Endpoint Detection & Response (EDR/XDR)
- Managed Security Service Provider (MSSP)
- Detection, Correlation, and Threat Response
- Managed Infosec Department Support
- Dark Web Intelligence Monitoring
Cyber Respond ServicesUnrivaled expertise through the entire incident lifecycle
- Digital Forensics & Incident Response
- Evidence Preservation and Reporting
- IT Asset Disposition
- Data Recovery
- Post-Incident Advisory
Cyber Advisory ServicesGuide clients toward higher digital maturity
- Technical & Policy-Based Digital Security Audits
- ISO 27001:2022 Compliance Advisory
- SOC Setup & Readiness Assessment
- Risk Assessment & Threat Modeling
- Virtual CISO (vCISO) Services
- Data Privacy & Protection (PDP) Solutions
Cybersecurity AwarenessStrengthen your human firewall
- Security Awareness Workshops
- Phishing-as-a-Service (Simulation & Training)
- Social Engineering Testing
- Ransomware & BEC Resilience Testing
- Executive Cyber Hygiene Coaching
Cybersecurity TrainingUpskilling programs for technical teams
- DevSecOps & DevOps Training
- Web & Mobile Penetration Testing Training
- Infrastructure Penetration Testing
- OSINT & Threat Intelligence Training
- Computer Forensics & Investigator Programs
Protecting the Visible
Comprehensive operational security services to safeguard your people, facilities, and physical assets.
Operational Planning & Risk DesignDesign operational security architecture from the ground up
- Site & Facility Risk Assessment
- Security Layout Consultation
- Integration Planning for Command Centers
Surveillance & Monitoring SystemsReal-time visibility through centralized monitoring
- CCTV & Alarm System Installation
- Environmental Monitoring (motion, smoke, flood)
- Central Command & Remote Surveillance Integration
Emergency & Incident ResponseEnd-to-end systems for incident response and recovery
- Alarm Escalation Protocols
- Crisis Management & Evacuation Planning
- Incident Documentation & Reporting
- Coordination with Local Law Enforcement
Access Control & Identity SystemsSecure, traceable, automated access management
- Smart Lock & Biometric Systems
- Entry Point Automation
- Visitor Management Systems
- Credential Lifecycle Tracking
OT / Smart Building SecurityProtecting the technology that runs your physical world
- IoT & Industrial System Hardening (SCADA, PLC, BMS)
- Network Segmentation for Building Infrastructure
- Continuous Vulnerability Testing for Connected Devices
- Energy, HVAC, and Sensor Security
Protection & Patrol ServicesTrained personnel integrated into your security system
- Static & Mobile Guarding
- Executive & Event Protection
- Patrol Reporting & Escalation Protocols
- 24/7 Command Center Integration
Security Training & AwarenessBuilding preparedness and confidence in your team
- Emergency Drills & Response Exercises
- Anti-Tailgating & Social Engineering Training
- On-Site Awareness & SOP Discipline Workshops
- Physical–Digital Joint Simulation Programs (Hybrid Drills)
Connected Security Experience
The Integration Layer represents the evolution of Sector‘s Total Security vision, uniting Digital Security and Security Operations into one seamless ecosystem.
While each domain already operates with precision and discipline, our long-term mission is to integrate them — creating connected systems, shared intelligence, and synchronized response.
What We're Doing Now
Capabilities
- Providing end-to-end security coverage, from digital defense to on-ground protection
- Establishing shared frameworks for communication and risk management
- Creating a unified client experience through single-point project coordination and reporting
What It Means for Clients
- One trusted partner for total protection
- Streamlined management and accountability
- Consistent standards across both digital and physical defense layers
What We'll Be Able to Do
Capabilities
- Integrated Training Programs, combining digital awareness, physical response, and leadership simulation
- Unified Security Audits, evaluating both cyber resilience and operational readiness in one framework
- Cross-Domain Response Procedures, linking SOC alerts to field actions and escalation playbooks
What It Means for Clients
- Cohesive defense systems across every layer
- Simplified audit and reporting processes
- Faster, better-coordinated response during incidents
What It Will Enable
Capabilities
- Unified Command & Monitoring, one dashboard connecting digital systems and operational control centers
- Threat Correlation Across Domains, linking dark web intelligence, network alerts, and physical incident data
- Automated Response Workflows, cyber alerts triggering facility lockdowns or on-site countermeasures
What It Means for Clients
- Real-time visibility across all assets, systems, and facilities
- Proactive defense instead of reactive response
- A truly Total Security Ecosystem, intelligent, seamless, and adaptive
Ready to Experience Total Security?
Let‘s create a peace of mind - together. Reach out for a complimentary consultation and assessment.
SectorOne
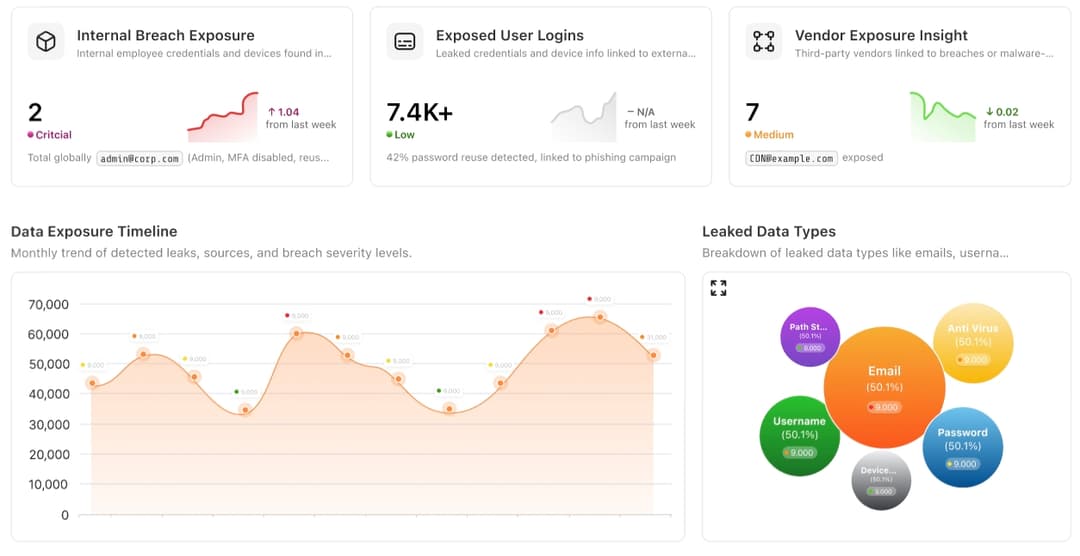
Threat Intelligence Platform
Peace of mind through proactive threat intelligence. Know about data breaches and vulnerabilities before they impact your business.
Dark Web Monitoring
Continuous monitoring of dark web marketplaces for your leaked data
Automated Data Leak Detection
Real-time alerts when your sensitive information appears online
Attack Surface Management
Comprehensive visibility into your digital attack surface
Vulnerability Intelligence
Interactive dashboard with prioritized threat intelligence
Now Available
- Real-time threat intelligence monitoring
- Dark web breach detection
- Comprehensive security dashboard
Creating Peace of Mind Across Industries
Trusted by leading organizations across different industries to achieve genuine cybersecurity peace of mind.
TRUSTED BY LEADING ORGANIZATIONS











Start Your Journey to Peace of Mind
Get a comprehensive security assessment tailored to your business. No fear tactics, just honest insights and actionable recommendations.